It’s not as easy as you think. You have to be very lucky to succeed. With promises of “free coins” and shady characters out to steal your keys, it’s no wonder even tech experts get nervous. This guide will help you avoid scams, whether you are an experienced crypto investor, a curious general user, or an older person finally looking into your crypto IRA. Learn the latest fraud tricks (2023-2025) used by scammers, along with practical and amusing tips to prevent scams. Put on your VPN cape and grab your hardware wallet shield to make your online crypto life impenetrable!
Dodging Crypto-Specific Scams: Fake DMs, Phishing Wallets, Giveaway Cons
Scammers love to sound legitimate. You may receive a “DM” on Twitter or Telegram from a celebrity or influencer who claims to be announcing a big “giveaway”—as if, for example, Elon Musk suddenly wants to send you free Bitcoin (phemex.com). These are fake. The real “Elon” is not sending DMs to random people with offers. They’ll ask you to click a link or even send them a tiny bit of crypto “to verify your wallet.” Do that, and poof, your money is gone, and they are gone too. The FTC warns that MetaMask phishing emails state your crypto will be lost if you don’t click on the email link. Those are scams, too.
To stay safe
• Verify, verify, verify. Always check the sender. Official crypto projects have verified social media accounts (look for the blue badges). When in doubt, go to the actual website (the one for MetaMask, for example, or the official channels for Coinbase) rather than clicking a random link (phemex.comconsumer.ftc.gov).
• Be careful of making any investments that promise free money. If one party claims to be offering free crypto in exchange for a small amount upfront, it’s almost certainly fake. As the saying goes, ‘If it looks too good to be true, it probably is.’ Similarly, no legitimate giveaway will ask you to send them crypto first (phemex.com).
• Fake websites and phishing extensions. Download wallets or extensions (such as MetaMask or Ledger Live) exclusively from their official websites (MetaMask [1] or Ledger[2] pages). Fake phishing sites or scam browser add-ons can steal your keys. Be sure the URL is correct (no mistakes or letters).
If you keep skeptical with the offers and use the official channels, you will block the scams.
Scam Alert: Rug Pulls, Fake Coins & Pump‑and‑Dump Schemes
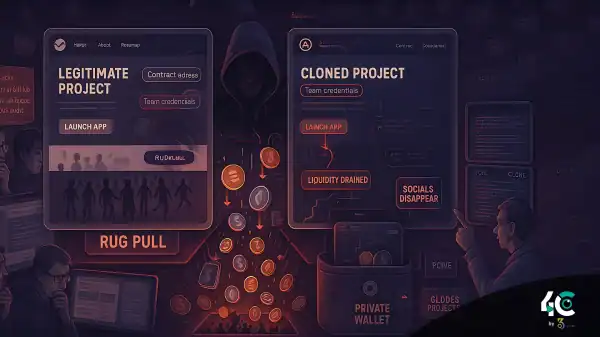
You need to be concerned not only about the shady characters but also about the potential disappearance of entire projects overnight. A rug pull refers to a scam where the developers of a cryptocurrency project suddenly withdraw all their funds and disappear, leaving investors with worthless tokens. In 2024, Jump Trading faced allegations of a pump-and-dump scheme involving the DIO token. The company allegedly used influencers to boost the token’s price, then cashed out, leaving the holders stranded (crypto.news). In 2024, we witnessed the classic manipulation of meme coins such as “FROGGY.”
In fact, it’s even more wild than that: researchers found that nearly 90% of the new tokens on the Base network Uniswap v2 pools were malicious “spray-and-pray” scam coins (metamask.io) used to scam people out of their funds. One scammer alone pushed over 19,000 fake tokens! Many of these scams have anonymous teams, fancy websites, and promises for “10x gains.”
How to survive these traps
• Do your homework. Before investing in any new cryptocurrency, please take a moment to verify the individuals or team behind it. Do they have real, verifiable profiles? Transparent teams and public code repositories usually characterize a successful project. A total mystery team is a red flag.
• Be cautious when using memecoins and airdrops. Be careful if a new coin launches and offers you a deal for huge gains. Likewise, be cautious if someone arbitrarily distributes coins. According to the report from MetaMask, these new tokens are essentially hard rug pulls. If the coin’s listing spikes overnight on dodgy exchanges (not the likes of Coinbase or Binance) and a few days later you see dozens of “investors” pumping its price, then it’s a pump-and-dump scam.
• Use reputable platforms. Use trusted exchanges (Coinbase, Kraken, etc.) and authorized DEXs. These have listing vetting. Even in these instances, verify any token contract on Etherscan or BSCScan. Trust but verify.
You keep your crypto assets from going away if you treat every new token with caution.
SIM Swap Scams: When Your Phone Number Gets Hijacked
You’re chilling on your couch, and your phone suddenly stops getting service. A few minutes later, your email is hacked, your exchange is drained, and the only telltale sign is a message saying, “Welcome to your new SIM!” Welcome to the SIM swap scam.
What is it? A SIM swap, also known as SIM hijacking, is when a hacker persuades your mobile carrier to transfer your phone number to their SIM card. If they control your number, they’ll get your text messages and calls, including 2FA codes sent by crypto exchanges or wallets. Now they can change your password and unlock your account.
A SIM swap attack that took only 7 minutes in real life cost a California man over $1.3 million in 2024. The hacker used the number to reset his login for Coinbase, drain the cash, and vanish down a crypto mixer (Washington Post).
Learn how to safeguard yourself against SIM swaps
• Don’t go for SMS-based 2FA for crypto. It’s too easy to hijack. You should either use an authenticator app like Authy or Google Authenticator or, preferably, a hardware 2FA key like YubiKey.
• Speak with your carrier about adding a PIN or password to your account, which they must provide before making any changes. You must ask Verizon, AT&T, or T-Mobile to enable it for you.
• Lock down your email. Your email is the reset point for everything. Lock it down with a strong password and 2FA (preferably app-based or hardware key).
• Use different emails and phone numbers. It’s a beneficial idea to have a number/email just for crypto, not linked to your public identity. Reduction in exposure leads to a decreased likelihood of targeting.
• Be Aware Of Unannounced Drops In Services. If your phone suddenly loses signal, especially when you’re not in a dead zone, this could be a sign of SIM hijacking. Please contact your provider, place a freeze on your accounts, and check for any suspicious activities.
Malware Menace: Guarding Against Crypto‑Stealing Malware
Even with smart browsing, your device can betray you. Clipboard hijackers and keyloggers lurk in the background looking for cryptocurrency. Clipboard hijackers keep an eye on when you copy a crypto address and replace it with an attacker’s address. (securityaffairs.com). You paste your friend’s wallet, and boom, the coins go to a scammer instead. Scientists professed that within the year of 2025, a malware known as TerraStealerV2 snatches stored wallet data from the browser, and a malware like TerraLogger is known to record every keystroke as 2025 approaches (thehackernews.com). Fraudulent wallets that steal your keys can even be “safe” Chrome extensions.
Stay safe with these steps
• Double-check pasted addresses. Please ensure you verify the beginning and ending letters of any crypto address you intend to paste. One wrong digit is a dead giveaway of a hijack.
• Use official software. Always download wallets (MetaMask), exchanges, and antivirus from their official websites only. No “free” wallet app on a random site. Never install random apps that “are for your Ledger” (it’s probably fake)—Ledger and Trezor, for instance, have official download pages.
• Limit browser extensions. Only retain extensions you trust (MetaMask, Ledger Live) and remove any you don’t use. Regularly audit them. Scammers sometimes publish fake wallet extensions that appear genuine. If an extension asks for private keys, cancel immediately.
• Use antivirus/anti-malware. Use an updated antivirus program (like Windows Defender or Malwarebytes) to prevent known crypto malware attacks. Always keep your operating system and browser up to date, as many attacks exploit old security holes.
• You should use hardware wallets for significant funds. Keep big balances on hardware wallets (Ledger, Trezor). These devices validate or sign the transaction data when offline, which means even if a computer is compromised, your private keys never leave them. Only utilize them with trustworthy apps (Ledger Live or Trezor Suite).
Being a little careful on your computer and mobile can do wonders. Think of each check as an extra lock on your digital door.
VPNs: Your Crypto Bodyguard (and How to Use Them Right)
Using a VPN can protect your cryptocurrency transactions in several ways (hide.me). This software keeps your internet traffic safe, making it difficult for hackers on the same network to spy on you. If you use Wi-Fi publicly (like in a café or airport), using a VPN would make sure that any hacker sharing the hotspot cannot see that you are logging into your wallet or exchange. A VPN prevents your ISP and ad tracking. Therefore, if the crypto exchange that is connected to your IP address experiences a data leak, you will still maintain a degree of anonymity (veepn.com).
However, beware of cheap tricks
• Choose a trusted VPN. NordVPN, ProtonVPN, Mullvad and other paid no-logs services are safer. Many free VPNs have poor security or even sell your data (eccu.edu). In fact, many free VPNs have been caught bundling malware or tracking you—exactly what you’re trying to avoid.
• Connect before accessing exchanges. When using unfamiliar wifi networks, ensure that you log in to your crypto account only after you have turned on your VPN. This adds an encrypted tunnel. According to hide.me’s guide, with a VPN on, “anyone monitoring your connection won’t be able to tell which apps you’re using, like cryptocurrency wallets” (hide.me).
• Use VPN kill-switch features. When your VPN disconnects, a kill switch prevents internet access to protect your unencrypted data. This is extra insurance for mobile trading.
• The use of a VPN alone is not enough. While VPNs improve privacy, they don’t stop phishing attacks and malware. You still need good antivirus and safe browsing habits. Visualize a VPN as an extra layer of armor, not the whole shield.
In short, a VPN (when used properly) is like a helmet and sunglasses—it won’t prevent every accident, but it blocks loads of peering eyes.
Fort Knox Your Crypto: Seed Phrases, Wallets, and Account Security
Finally, let’s secure your keys and accounts expertly.
• Never share seed phrases (recovery phrases). Not even with friends or “support.” Don’t tell anyone your 24 words of their recovery phrase under any circumstances. Ledger (ledger.com) Keep them written on paper (or backed up on metal devices), not online or in a picture. Keep that backup in a secure location (fireproof box or safety deposit box). It’s risky to remember them. It’s unsafe to write them on a Post-it (or in a file).
• Use a Ledger [2] or a Trezor [3] for significant holdings. Purchasing directly from the official site prevents tampering with devices. Keep firmware updated. Please remember Ledger’s motto: if someone requests to “unlock” your device or verify your backup via phone or email, kindly disconnect the call. Don’t answer calls from someone who says they’re with Ledger.
• Enable 2FA (two-factor authentication) on everything. You better know what this means! It is better to use an authenticator app such as Google Authenticator or Authy. One also has the option of using a 2FA hardware key like YubiKey. Do not fully rely on SMS, as the SIM can be swapped.
Every account must have a unique password. There should not be password reuse! The best password is a password manager-generated one stored in a password manager (wired.com).
• System apps minimize the need for third-party apps—use browsers instead of Chrome, use the system gallery to organize pictures, etc. First utilizing all built-in features before adding another bloatware is a good idea. Wired describes Bitwarden as being “secure, open source, and free with no limits” (wired.com)—perfect for managing cryptic keys and logins. If you have a password manager, you only need to remember one (just make it really good).
• Cold storage means to keep only a small amount in online/hot wallets/exchanges. The rest goes offline. A hardware or paper wallet saved securely can be viewed as cold storage. You’ve been keeping gold bars in a safe and using only digital coins in your pocket for a while now.
• Regularly update your software, including your wallet software and operating system, to fix vulnerabilities.
Be wary of strange activity on your account. If you notice anything unusual, such as an unfamiliar login, please take prompt action. Change your passwords. Revoke app authorizations.
If you treat your crypto keys like real treasure (because they are!), thieves will have a hard time stealing them. A security report from MetaMask dated 2025 reminds you that scammers use every trick in the book. Strong 2FA, cold storage, and safe practices raise the bar sky high (metamask.iowired.com).
Action Steps: Be the Crypto Survivor
1. Triple-check senders. Double-check you’re using the right wallets and apps, or else you could lose it all. Watch out for incorrect grammar or spammy domains.
2. Update and armor up. Keep your devices patched, embrace antivirus, and only use VPN on public Wi-Fi and trusted wallets/extensions.
3. Lock up your secrets. For safety, use hardware wallets, enable 2FA everywhere, and store seed phrases offline.
4. Keep learning. Scams evolve fast. Follow trustworthy crypto news or alerts (FTC, Chainalysis, Metamask blog) so you hear about new tricks. Be alert; the IC3 of the FBI warned of a surge in cryptocurrency fraud in 2024.
Remember: in crypto, carefulness is your currency. No system is perfect, but if you do not accept “gifts”, check the address twice before sending money, and use security tools (VPN, hardware wallet, password manager), the hunter becomes the hunted. Keep your eyes peeled so no scammer can trick you! Let us make 2025 the year scammers get the cold shoulder.
Use latest security reports and guides by the FTC—consumer.ftc.gov, Ledger – ledger.com, MetaMask – metamask.io, cybersecurity blogs – securityaffairs.comthehackernews.com; products sites – Ledger – ledger.com, Trezor – trezor.io, MetaMask – metamask.io, Coinbase – coinbase.com and password manager – Bitwarden – bitwarden.com. These informed our tips above. Stay safe and happy hodling!