The Growing Threat of Blockchain Scams
It is safe to say that blockchain technology is one which aims for decentralization, transparency, and security. Despite this, it has become easier for malicious actors to exploit blockchain technology for their own benefit. Common threats include:
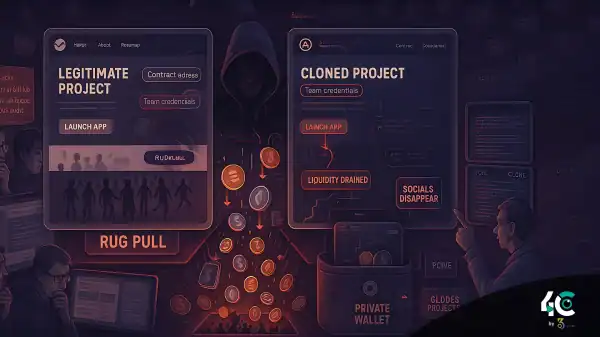
- Developers abandon the project after raising funds, leaving worthless token in its place.
- Honeypot contracts: They are smart contracts that trap users’ funds and do not allow them to withdraw their funds.
- Using algorithm manipulation to exploit liquidity pools: Flash loan attacks.
- A phishing scam involves fake sites and social profiles impersonating a given project.
In the year 2022 alone, DeFi exploits saw the losses of more than $3 billion. Hence, there is a dire need for solutions.
According to AI-enabled on-chain bots, neutralizing these extensions can prevent harm.
How AI Tools Detect Suspicious Activity
AI-based tools find problems in blockchain networks and smart contracts. Below are the primary methods used:
1. Static Code Analysis
Without the need to run the code, we analyse the source code of smart contract. AI models know that thousands of vulnerabilities are already known and vulnerable. They can identify harmful malicious intent patterns.
- Lack of withdrawal functions in honeypot contracts.
- Governance and control are with central authorities.
- Unusual tokenomics that favor developers over users.
2. Dynamic Behavior Monitoring
Observers can investigate the execution of smart contracts by using dynamic analysis. AI bots keep an eye on everything from wallets to contracts to dApps, flagging irregularities such as:
- Large transfers shortly after contract deployment.
- A sudden increase in trading volume is a sign of a pump and dump.
- Gas usage indicates that the code is bad.
3. Anomaly Detection
Machine learning models are noting the current blockchain activity in relation to historical baselines. For example:
- A wallet that does many high-value transactions can be hacked.
- If there is an unusually clustered pattern, it could be Sybil attacks or wash trading.
4. Natural Language Processing (NLP)
AI tools analyse project whitepapers, docs, social media posts, and more through NLP to filter these out. We consider projects with unclear roadmaps or too much marketing language to be higher risk.
Leading AI-Powered Scam Detection Tools
There are new platforms that are in trend to fight against blockchain frauds. Here’s a closer look at some of the most impactful tools.
1. CertiK Skynet
Software combines static code examination with real-time on-chain activity monitoring to conduct its operations.
Key Features:
- Keeps an eye on wallet actions, summoning history and community sentiment.
- Presents a “trust score” for outcomes based on aggregated data.
- Users may face threats via dashboards and alerts.
CertiK has flagged billions of dollars’ worth of fraud including protocols like PancakeSwap and Aave.
Decentralized AI-driven bots network with useful functions, community-supported.
Key Features:
- Bots search for specific threat types, such as flash loan attacks or unauthorized admin actions.
- Developers can create detection rules with open-source architecture.
- Helps quickly respond to emerging threats.
Impact: Forta detected multiple incidents, including an attempted $10 million exploit in 2023.
It aids in tracking the illicit transfer of money on all blockchains.
Key Features:
- Shows how criminal wallets are connected to each other.
- Works with law enforcement to recover stolen property.
- Offers predictive analytics to anticipate future attacks.
Chainalysis is used by regulators and exchanges to stop money laundering and terrorism financing.
This tool specializes in automatically auditing and protecting smart contracts while they are running.
Key Features:
- Identifies vulnerabilities during development phases.
- Monitors deployed contracts for signs of exploitation.
- Generates detailed reports with actionable recommendations.
Impact: Focused on preemptive measures to avoid catastrophic failures before they hit production.
Case Study of Using AI to Stop Rug Pulls
To demonstrate the utility of these tools, let’s take a hypothetical example of a fresh DeFi protocol.
Phase 1: Deployment
An anonymous group launches a yield farming platform with high APYs. The smart contract is deployed without an audit.
Phase 2: AI Analysis
- Centralized minting detected by CertiK Skynet, indicating rug pull risk.
- Forta flags LP hoarding wallets through behavioral monitoring.
- NLP shows deceptive marketing language and unclear promises.
Phase 3: Intervention
Users and exchanges are alerted. Investors exit before developers can perform a rug pull, saving millions.
Challenges Facing AI Scam Hunters
Although these tools can do a lot, there are hurdles.
1. Evolving Tactics
Scammers constantly adapt to evade detection. AI models need continual updating.
2. False Positives
Too many alerts could desensitize users or flag legitimate projects.
3. Scalability Issues
Growing blockchain data demands more processing resources.
4. Regulatory Gaps
Inconsistent global standards complicate cooperation and enforcement.
Final Thoughts: Strengthening Web3 Security
AI bots are chasing after harmful activity on the chain. Through potent monitoring and analytics, it helps the user make important decisions and scare away harmful actors.
However, no single solution can eliminate all risks. A cooperative defense must involve engineers, auditors, regulators, and users. As AI improves, it will secure blockchains and establish trust and sustainability in Web3. This helps protect users from market manipulation and hacking.
Conclusion
Introducing AI utility tools for scam detection techniques like CertiK Skynet, Forta Network, and Chainalysis Reactor that revolutionize the way we detect scams through smart contract analysis, on-chain behavior monitoring, and detecting malicious activity through machine learning. System processes are responsible for blocking attacks, protecting users, and enhancing overall security. Though there are obstacles like spoofing and false positives, the new introduction of these defenses is an important first step towards preserving decentralized tech and enabling safer interaction.