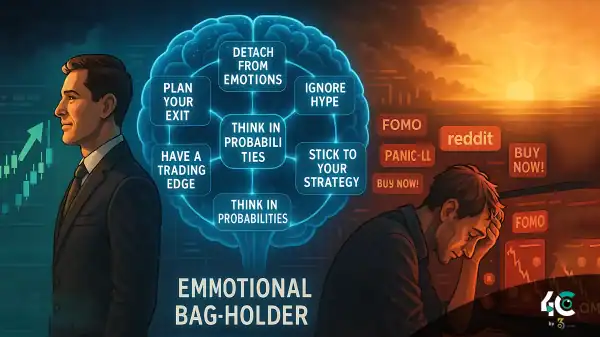
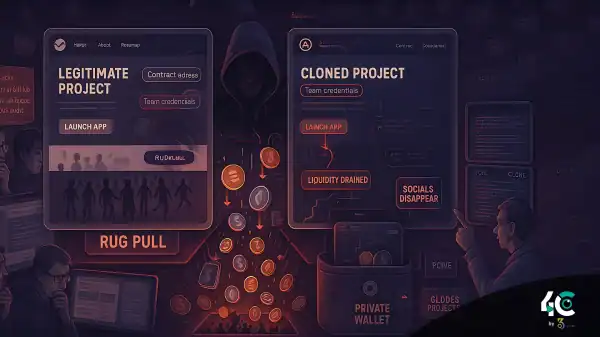
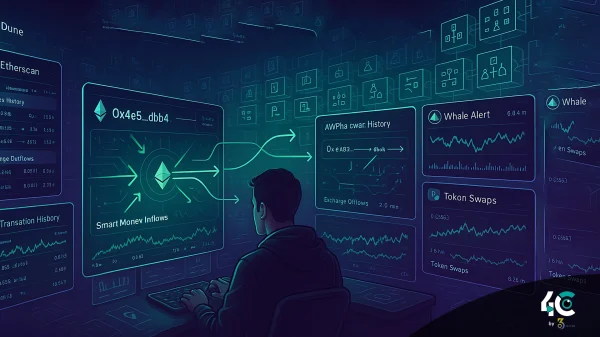
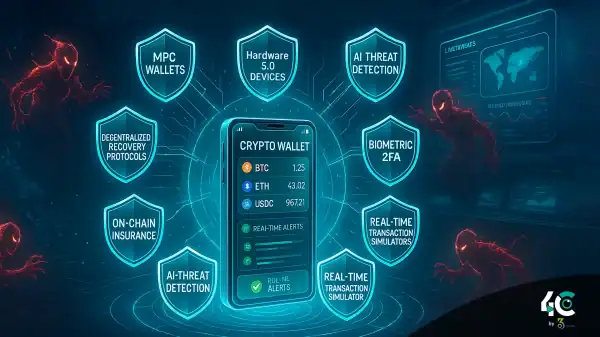
A massive cybersecurity breach has sent shockwaves through the tech and crypto industries after 16 billion login credentials were leaked from major platforms including Apple, Google, Facebook, Telegram, and various government services.
According to researchers at Cybernews, the breach involves data from 30 different datasets, each ranging between 16 million to 3.5 billion records. Experts say this may be the largest exposure of credentials in history.
Origins of the Breach
The leaked data likely came from infostealer malware, malicious software that steals usernames and passwords from infected devices. Much of the data was exposed via misconfigured Elasticsearch servers and unsecured object-storage systems—vulnerabilities that allow unauthorized access to vast amounts of sensitive information.
The leaked records include usernames, passwords, cookies, tokens, and metadata, which together can be used to compromise nearly any digital account—from personal emails to critical government portals.
“This is not just a leak but a toolkit for the crooks,” researchers stated. “With this new data, we’re entering a new phase of mass account takeovers, identity theft, and phishing scams.”
Crypto Industry Faces Elevated Risk
The leak poses a unique threat to cryptocurrency users. Hackers may exploit this information to access:
- Custodial wallets
- Email-linked wallets
- Seed phrases or backups stored on cloud services like Google Drive
Security researchers confirm that credential-stuffing attacks are already targeting crypto platforms, potentially leading to large-scale theft and forcing companies to reset user credentials or suspend access entirely.
Weak Password Habits Amplify the Risk
The breach highlights a major ongoing issue: poor password hygiene. Many users continue to reuse weak passwords across multiple platforms, leaving them vulnerable to automated attacks that test leaked credentials against common platforms—a tactic known as credential stuffing.
What Users Should Do Now
Cybersecurity experts recommend urgent action, especially for users involved in crypto:
- Change passwords for all critical accounts—especially email, exchanges, and financial services.
- Enable two-factor authentication (2FA) on every platform that offers it.
- Never store private keys or recovery phrases in cloud services.
- Use a trusted password manager to generate and store strong, unique passwords.
Conclusion
This record-breaking breach underlines the growing sophistication of modern cyber threats. With billions of compromised credentials now circulating online, individuals, businesses, and especially crypto holders must act quickly to safeguard their assets and identity.
The source of the leak remains unknown. But regardless of its origin, this event proves that in the digital age, cybersecurity is not optional—it’s essential.