The crypto world is incredibly fast-paced and constantly innovating. But not every project survives the hype cycle. When ecosystems age and tokens die, a lot of coders abduct their codes and leave empty shells.
But recently something strange has been going on; some unknown developers are bringing these dead projects back to life in the dark. Welcome to the world of shadow forks.
What Is a Shadow Fork?
A shadow fork typically refers to an unauthorized clone or revival of an abandoned or inactive crypto project, usually by a fresh team of anonymous developers. These developers usually take the original open-source codebase and launch their own version, claiming to “save” the project or unlock new utility.
Shadow forks are not typically publicized or formally documented. This is in contrast to forks like Ethereum, which has two coins, where the original community was on board with the split.
Why It’s Happening
Low barrier of entry: Since many older DeFi or Layer-1 projects are open source and hosted on GitHub. Anyone can copy the code and deploy it without much effort.
“This shadow fork impacts projects that had once gathered a decent following.” To quickly catch the eye and attract liquidity, developers exploit this.
Airdrop Farming: By forking a dead token, you can cause airdrop hunters to scramble for positions. Then it can start hype with very little development effort.
Some malicious actors shadow fork projects only to perform pump and dump schemes or to siphon funds via hidden smart contract backdoors.
Risks for Users
It might be easier to use a revival project, especially if they promise innovation or a return to the good old days. But shadow forks do come with some serious red flags.
No Audit or Oversight: Changes may be made to contracts in dangerous ways—a new team whose members often remain anonymous.
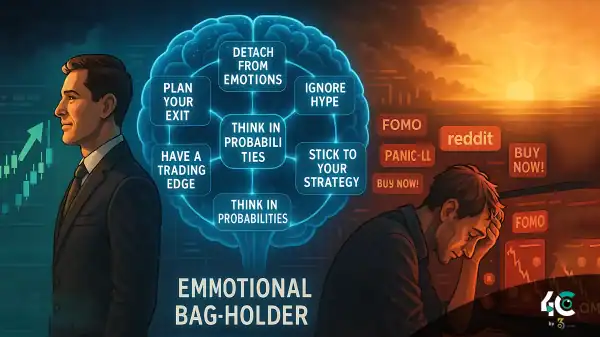
Changing the name of an obsolete project doesn’t create a new future. Nor does it provide real utility.
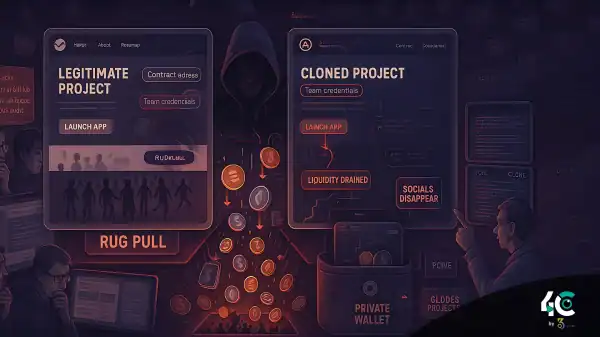
Rug pulls refer to instances when developers drain the liquidity pool of a cryptocurrency project.
Forked projects can mix up original holders and create confusion about which project is the “real” one.
Real-World Examples
Recently there were examples of shadow forks of tokens long forgotten that spiked but faded away quickly as their motives were unveiled. Some copied entire ecosystems with minor UI updates. Some others introduced new tokenomics and governance tokens, later locking users’ funds or disappearing.
How to Stay Safe
Detecting an early shadow fork is important for traders and investors. Here are some tips:
- Take a look at the GitHub activity and age of the contract. Sudden activity after years of silence is a red flag.
- Who’s the team? Are They Doxxed? Linked to the original devs? Or totally anonymous?
- If there was no audit of the smart contract, the code was not transparent, simply avoid it.
- Don’t fall for the hype of the latest meme project or nostalgia. Legit forks usually offer real utility or upgrades.
Conclusion
The shadow fork shows that nothing ever dies in crypto. But some things that come back to life are worth ignoring. While some forks may truly wish to improve the past, many simply take advantage of the ambiguity about abandoned ones.
Shadow forks may straddle the line between innovation and exploitation in a space built on decentralization and open-source value.
No matter how authentic the project seems, always do your own research (DYOR) and don’t chase shadows.